Burpsuite and browser tricks
Burpsuite
Burp certificate
Burp Shortcuts
Install Custom Burp Extentions
Enable response interception

Burp Match and Replace
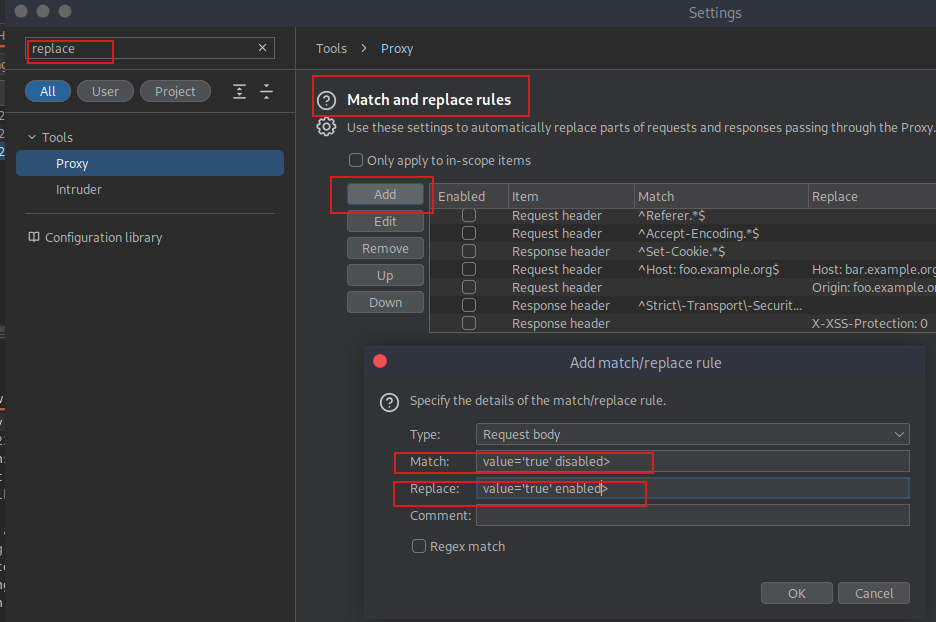
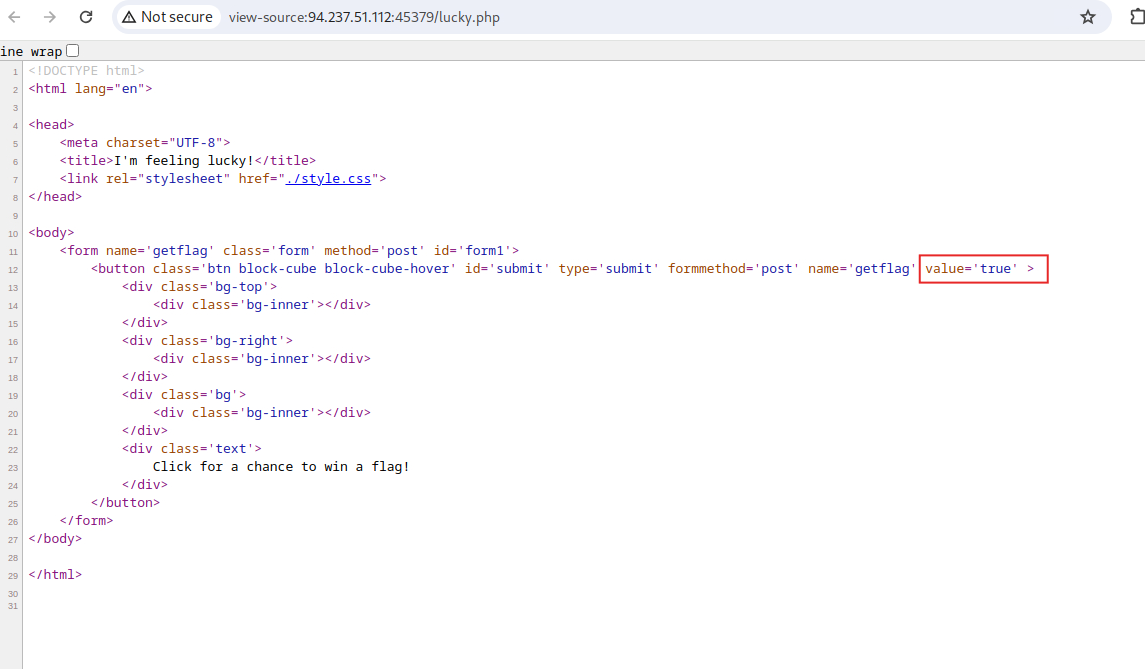
Session Handling Rules

Reporting
Burp extensions
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
Extentions
Extensions
Extension
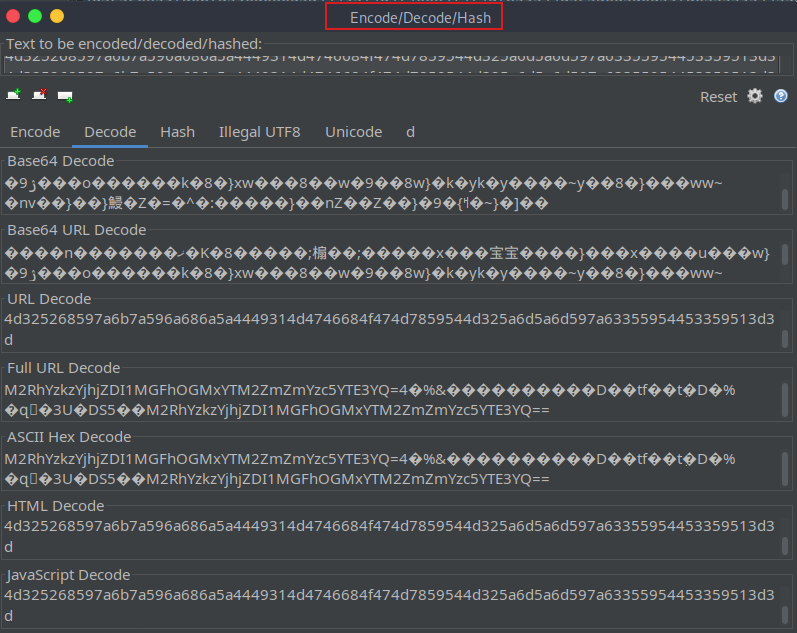
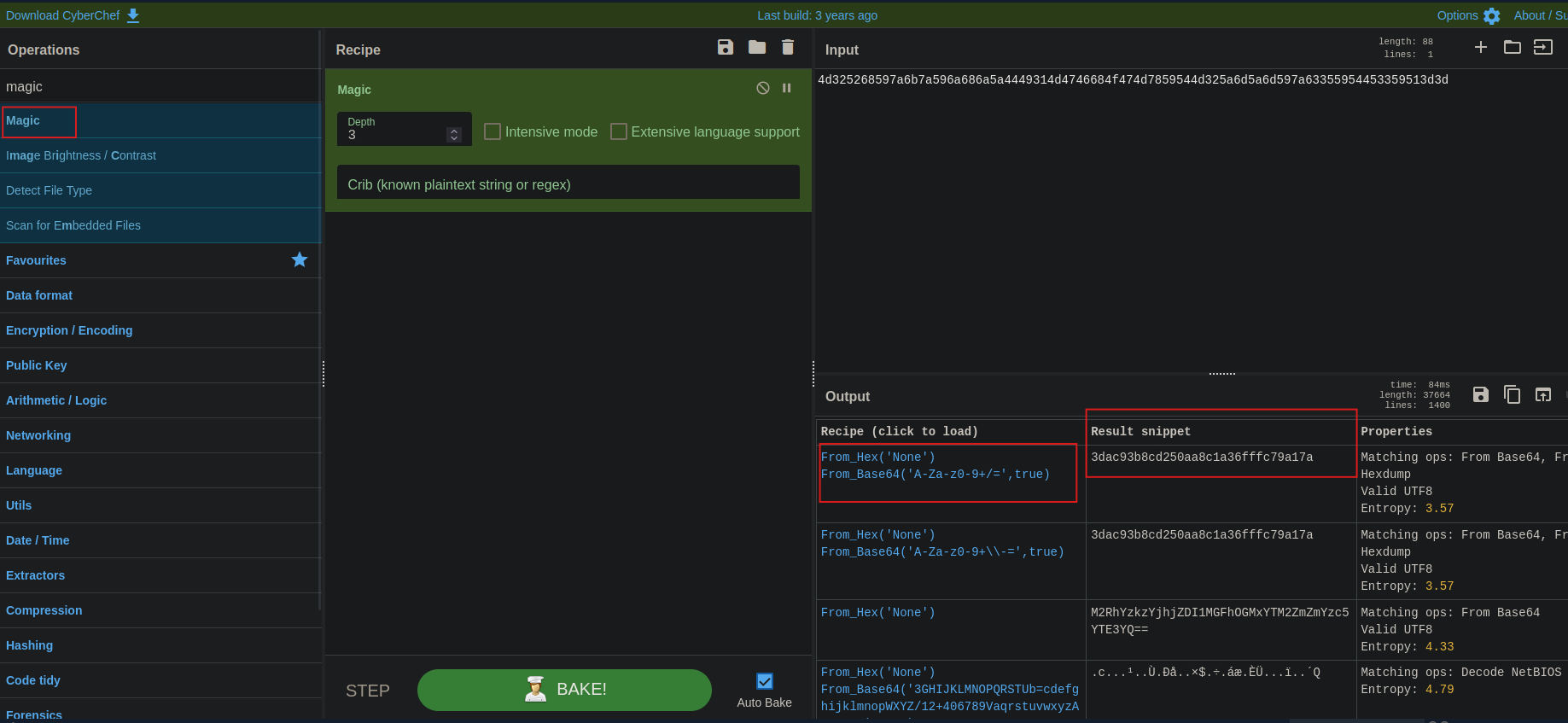
Decoder - Encode/hash/Decode ZAP
Intruder
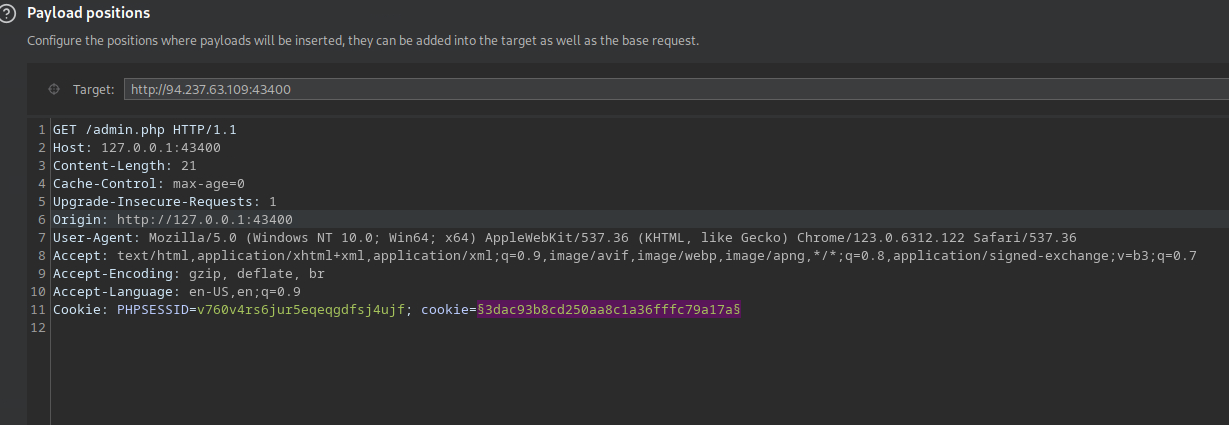
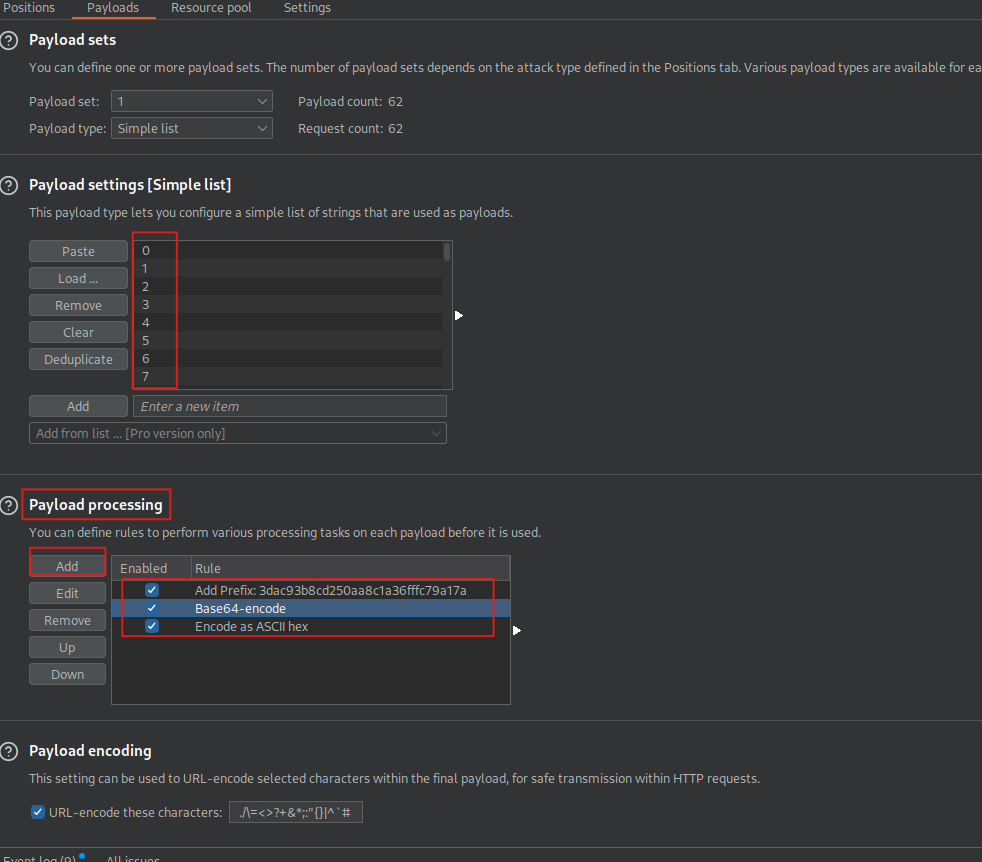
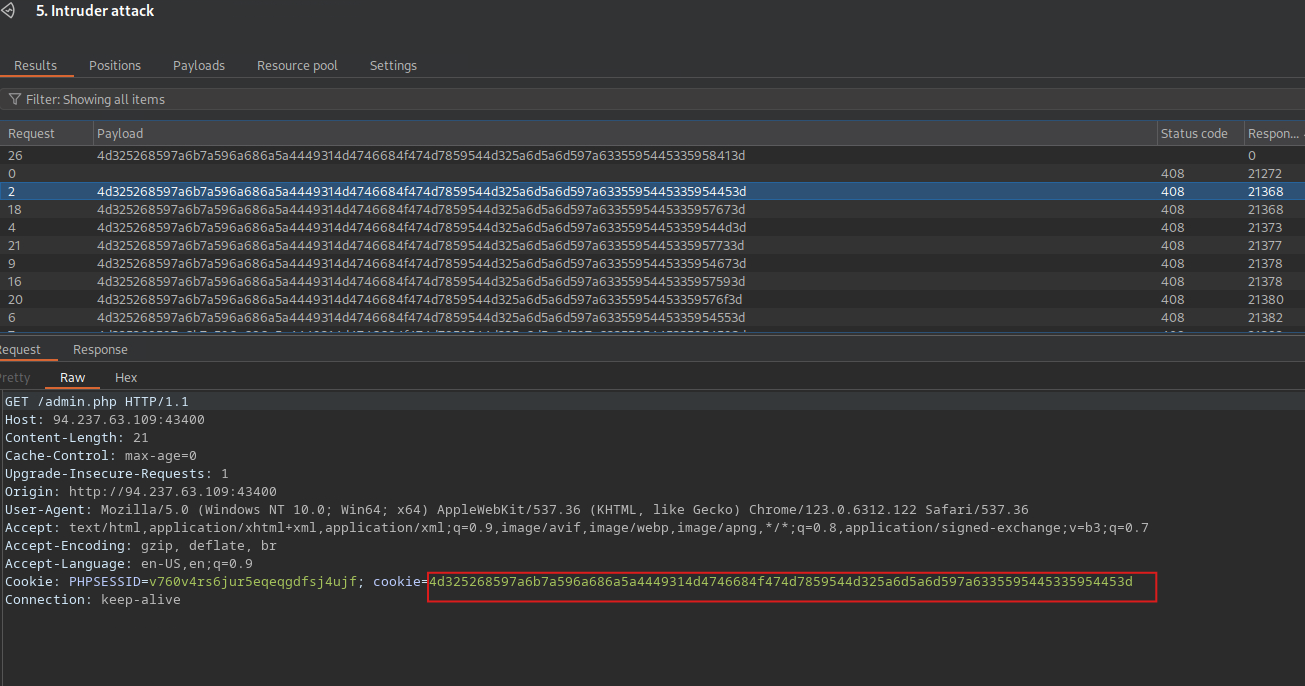
MetasploitToBurp
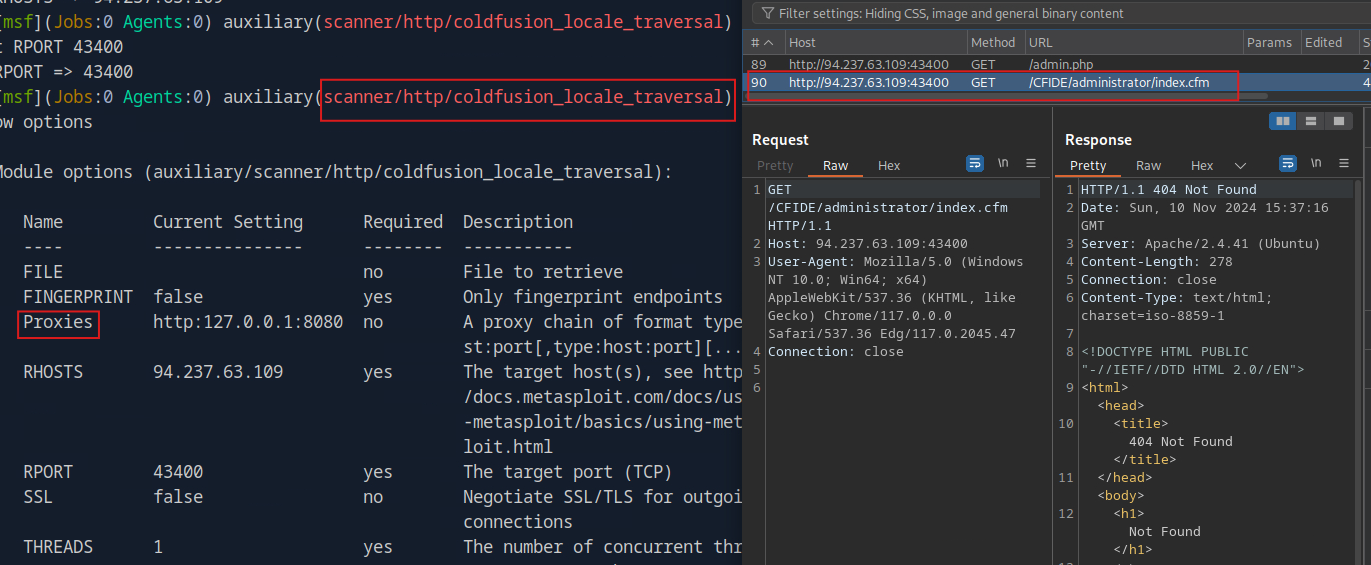
Browser console tricks
Browser DevTools
Get Local storage via console:
Export Local Storage:
Import Local Storage:
Last updated